)
Tor Browser
Pacote de ferramentas para quem deseja segurança e anonimato na internet
Pacote de ferramentas para quem deseja segurança e anonimato na internet
Sobre o App
Por Renan Hamann
Atualizado em 30/08/2023 02h06minTor é um pacote de ferramentas para organizações e pessoas que desejam mais segurança na internet. Usando-o, o tráfego de dados gerado por mensageiros instantâneos, navegadores, SSH e outros aplicativos que usam o protocolo TCP se torna anônimo.
O programa funciona a partir de um grande conjunto de servidores, mantidos por usuários para manter a privacidade durante a navegação, bem como eliminar a censura de conteúdos.O Tor também fornece uma plataforma na qual os desenvolvedores podem construir novos aplicativos baseados no anonimato, segurança e privacidade.
O tráfego é mais seguro ao usar o Tor, pois as comunicações são ligadas através de uma rede distribuída de servidores, chamados roteadores onion (Onion Router), um projeto que visa a proteção e o direito do usuário de permanecer anônimo na internet.
Em vez de direcionar a rota da fonte para o destino, os pacotes de dados da rede Tor assumem um caminho aleatório através de vários servidores que cobrem os traços para que nenhum observador inoportuno saiba de onde vieram e para onde vão. O propósito dessa tecnologia é proteger os usuários da internet contra a "análise de tráfego", uma forma de monitoramento de rede que ameaça o anonimato e a privacidade, atividades comerciais confidenciais e relacionamentos, além da segurança de Estado.
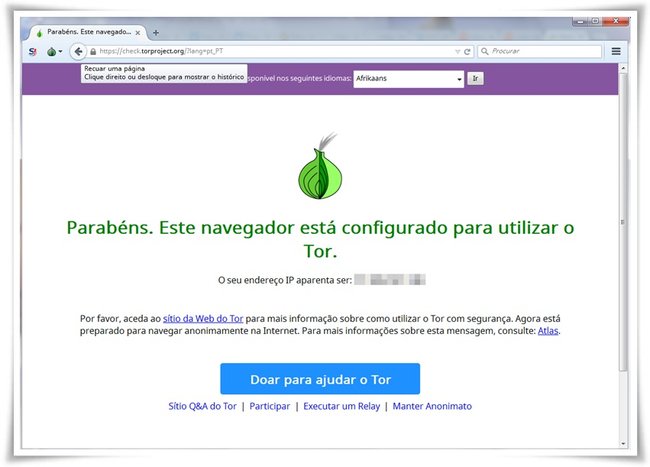
Interface gráfica e configurações
A interface gráfica do Tor chama-se Vidalia. Ela é instalada automaticamente e permite que o usuário acesse as configurações do aplicativo com facilidade.
Além disso, um complemento para o navegador Firefox permite habilitar/desabilitar a utilização do Tor durante a navegação; trata-se do Tor Button, que é gratuito e está incluído na instalação.
Análise de tráfego
A análise de tráfego — também conhecida por traffic shaping — é usada diariamente por corporações, governos e indivíduos que desejam manter um banco de dados do que fazem pessoas e organizações na internet. Em vez de procurar o teor das comunicações, a análise de tráfego rastreia de onde vêm e para onde vão os seus dados, assim como quando foram enviados e a quantidade.
Por exemplo, companhias usam a análise de tráfego para armazenar um registro de que páginas da internet você visitou para construir um perfil dos seus interesses. Vamos supor que uma indústria farmacêutica use essa análise ao pesquisar um nicho de mercado, monitorando o website do concorrente para saber quais produtos interessam a você. Uma lista de patentes pode ser consultada, rastreando todas as buscas feitas.

Uma das grandes vantagens é que o Tor dificulta a análise de tráfego ao evitar o rastreamento de dados online, permitindo que você decida se deseja se identificar ou não ao se comunicar. A segurança é aperfeiçoada enquanto mais pessoas se voluntariam a executar servidores. Parte do objetivo do projeto Tor é fazer um experimento com o público, ensinando as melhores saídas para obter privacidade online.
Opinião dos editores
Notícias
Informações Técnicas
Plataforma
WindowsTamanho do app
53.81 MBLançado em
2018-11-07 14:18:01.537Oferecido por
Roger DingledineContato da Empresa
Acessar site
Assistir vídeo?
Seu download vai começar após o anúncio.